Finally, as drastic as it seems, if your computer has been infected with a large number of spyware programs, the only solution you may have is backing up your data, and performing a complete reinstall of the operating system.
Monday, May 19, 2008
And, when all else fails?
So what do you do about it?
No spyware program seems to do everything, but there are a lot of goods solutions out there that can help. Here is a list of some of the top Spyware tools to look at:
1) Try Ad-Aware 6.0 Professional from LavaSoft (there is also a free version with less functionality)
2) Spybot Search & Destroy from PepiMK Software
3) Xoftspy form Pareto Logic
5) Spyware Guard from Javacool Software is a free program
4) Pest Patrol (now part of Computer Associates by acquisition)
5) McAfee Anti-Spyware
One thing is for certain: you do need to take spyware seriously. For some reason, too many people out there think anti-virus solutions are the end-all solution. They are not.
What is Spyware?
“The term ‘spyware’ is broadly defined as any program that gets into your computer without permission and hides in the background while it makes unwanted changes to your user experience.
Spyware is generally not designed to damage your computer. The damage it does is more a by-product of its main mission, which is to serve you targeted advertisements or make your browser display certain sites or search results.
At present, most spyware targets only the Windows operating system (Internet Explorer).”
To be fair, spyware can be harmless, for example tracking cookies don’t do much. While such things infringe on your privacy, they don't really harm anything. Others, however, are extremely dangerous.
How many spyware items are infecting your computer?
I just had, by mistake, a plug-in called Intelligent Explorer attach to my browser. What a nightmare! I have another article on this topic, but this brings home a point. Spyware or adware items are continually infecting computers. Most computers have no protection from them. Most frightening is the frequency of them. From the InfosecWriters web site, "According to a 2004 survey by America Online and the National Cyber Security Alliance, 91% of users questioned were familiar with the term spyware. Only 53% believed their computers were infected, but a scan found that 80% of their PCs had some type of spyware installed on them." It goes on to say, "...The average number of spyware components per computer was 93 with one computer having well over a thousand."
Trojan Horse….Greek Myth or Computer Nemesis?
We have all heard the term Trojan Horse, but what exactly is it? A Trojan Horse is a destructive program that masquerades as a harmless application. Unlike viruses, Trojan Horses do not replicate themselves, but they can be just as destructive. One of the most dangerous examples of a Trojan is a program that promises to rid your computer of viruses but instead introduces viruses into your computer.
The Trojan can be tricky. Who hasn’t been online and had an advertisement pop up claiming to be able to rid your computer of some nasty virus? Or, even more frightening, you receive an email that claims to be alerting you to a new virus that can threaten your computer. The sender promises to quickly eradicate, or protect, your computer from viruses if you simply download their “free”, attached software into your computer. You may be skeptical but the software looks legitimate and the company sounds reputable. You proceed to take them up on their offer and download the software. In doing so, you have just potentially exposed yourself to a massive headache and your computer to a laundry list of ailments.
When a Trojan is activated, numerous things can happen. Some Trojans are more annoying than malicious. Some of the less annoying Trojans may choose to change your desktop settings or add silly desktop icons. The more serious Trojans can erase or overwrite data on your computer, corrupt files, spread other malware such as viruses, spy on the user of a computer and secretly report data like browsing habits to other people, log keystrokes to steal information such as passwords and credit card numbers, phish for bank account details (which can be used for criminal activities), and even install a backdoor into your computer system so that they can come and go as they please.
To increase your odds of not encountering a Trojan, follow these guidelines.
1. Remain diligent
Trojans can infect your computer through rogue websites, instant messaging, and emails with attachments. Do not download anything into your computer unless you are 100 percent sure of its sender or source.
2. Ensure that your operating system is always up-to-date. If you are running a Microsoft Windows operating system, this is essential.
3. Install reliable anti-virus software. It is also important that you download any updates frequently to catch all new Trojan Horses, viruses, and worms. Be sure that the anti-virus program that you choose can also scan e-mails and files downloaded through the internet.
4. Consider installing a firewall. A firewall is a system that prevents unauthorized use and access to your computer. A firewall is not going to eliminate your computer virus problems, but when used in conjunction with regular operating system updates and reliable anti-virus software, it can provide additional security and protection for your computer.
Nothing can guarantee the security of your computer 100 percent. However, you can continue to improve your computer's security and decrease the possibility of infection by consistently following these guidelines.
Sunday, April 27, 2008
Retrieve Your Lost Windows XP Product Key
"Product Key: xxxxx-xxxxx-xxxxx-xxxxx-xxxx". Well if you can't find the Unattend.txt don't cry there's always another way to find out. On the same folder I386 there's a .SIF file that contains your Product Key. Its called WINNT.SIF. Right Click on it and select Open With... Notepad. Scroll down until you see this:
[UserData]
ProductKey = "xxxxx-xxxxx-xxxxx-xxxxx-xxxxx"
FullName = "Administrator"
Cheers!
Monday, April 21, 2008
Decrease your application start up
Example #1
You have AOL 8.0 installed on the computer. Complete the steps outlined bewlo to add the /prefetch:1 switch to AOL's Target path.
1. Right click on the AOL shortcut and select properties from the menu.
2. In the Target: Field add the /prefetch:1 switch to the very end of the path, like this: "C:\Program Files\America Online 8.0\aol.exe" /prefetch:1 and then click ok.
Now start AOL. It would load at least 50 times faster than ever before.
Example #2
1, Go to the Start button/All Programs/Accessories/System Tools
2. Right click on System Restore and select properties from the menu that appears. Add the /prefetch:1 to the Target Path entry so it looks like this %ystemRoot%\System32\restore\rstrui.exe /prefetch:1 and click ok.
Now System Restore will start immediately when executed.
Note: This switch will only work with some programs. Others will return a message saying the program in the target box is invalid. Just remove the switch
Wednesday, April 16, 2008
Adjust Graphics For Speed
To get started, Let's reduce the color quality. This setting determines how many colors are displayed on your screen.
1. Right click on your desktop and select properties.
2. Click on the settings tab and adjust the color quality drop down box to Medium (16 Bit).
3. Click OK.
Next, let's use the windows performance settings to optimize your computer for performance. This will revert back to the old Windows 2000 look as well as take away a lot of the fancy graphics effects. However, if you are really into performance, this is the price you have to pay.
1. Right click on the My Computer icon on your desktop or in your start panel and select properties.
2. Next, Click on the Advanced tab and hit the setting button under performance.
3. On the visual effects tab, select Adjust for Best Performance and hit OK.
4. Hit OK once more to exit system properties.
Now your computer will run slightly faster!
Monday, April 14, 2008
Speed Up your Firefox
1. Open your Firefox browser.
2. In the address bar, replace the web address with about:config as shown in the screenie.
3. Input the following by:
- double clicking the preference if it is present by default
- right clicking anywhere in the browser then go to New then Integer or Boolean if the preference is absent by default
Remember: if the value is a number, it’s an “Integer”. If it is either True or False, it’s “Boolean”. (Please click the word for the complete definition.)
Input without the comma.
browser.cache.disk.capacity, 15000
browser.cache.disk.enable, true
browser.cache.memory.capacity, 65536
browser.cache.memory.enable, true
browser.search.openintab, true
browser.tabs.loadFolderAndReplace, false
browser.urlbar.hideGoButton, true
config.trim_on_minimize, true
content.interrupt.parsing, true
content.max.tokenizing.time, 2250000
content.notify.backoffcount, 5
content.notify.interval, 750000
content.notify.ontimer, true
content.switch.threshold, 750000
network.http.max-connections, 48
network.http.max-connections-per-server, 16
network.http.max-persistent-connections-per-proxy, 16
network.http.max-persistent-connections-per-server, 8
network.http.pipelining, true
network.http.pipelining.maxrequests, 8
network.http.proxy.pipelining, true
network.http.request.max-start-delay, 0
nglayout.initialpaint.delay, 0
plugin.expose_full_path, true
ui.scrollToClick, true
ui.submenuDelay, 0
Double check, then close Firefox.
Open the bowser again. Firefox must speed up now.
Friday, April 11, 2008
Increase Your Hard Disk Speed
This tip is only recommended if you have 256MB RAM or higher.
Follow these steps:
Run SYSEDIT.EXE from the Run command.
Expand the system.ini file window.
Scroll down almost to the end of the file till you find a line called [386enh].
Press Enter to make one blank line, and in that line type
Irq14=4096
Note: This line IS CASE SENSITIVE!!!
Click on the File menu, then choose Save.
Close SYSEDIT and reboot your computer.
Done. Speed improvement will be noticed after the computer reboots.
Update: The most speed improvement is visible with IDE drives, however there are reports that this tweak also does good for SCSI disks. In any case, it won't harm your system, so why not try it yourself.
Wednesday, April 9, 2008
Useful Yahoo Commands
/cls clears the screen
/save saves the current chat session transcript
/leave exits current room
/join roomname joins roomname
/goto username joins the chat room that username is currently in
/follow username user will follows username whenever the user changes rooms
/think text posts text in this format "oO(text)"
/tell username text -- allows you to send a text to username with opening a window
/invite username invites username to the current room
/webcam starts your webcam
/version displays the program version
/version username sends the program version to username
/time shows the time
/roll number rolls the number of dice
/logoff closes the client
/ignore add username will add username to your ignore list
/ignore remove username will remove username from your ignore list
Monday, April 7, 2008
End Task Is not Fast Enough
Friday, April 4, 2008
Control Your System's Behavior
Ok let’s get started.
Preventing access to the command prompt
Click start > run and type gpedit.msc
Select the User Configuration.
On the right panel double click the Administrative Templates folder.
Now you should have at least 7 folders on the right panel including the System folder.
Open up the System folder on the right panel.
I think you’re starting to figure out which one are we going to select. Yes! You’re right it’s the Prevent access to the command prompt. Double click it and it will give you 3 radio buttons.
1. Not configured
2. Enable
3. Disable
Select/check the enable button (this will enable the Disable the command prompt script processing also? drop down list)
Go the drop down list and choose Yes. Click apply or OK. Don’t leave the GPEDITOR yet. To Undo the changes just select the Not configured button.
Let’s test it.
Click start > run and type cmd
You should see something like this:
“The command prompt has been disabled by your administrator
Press any key to continue…”
Some system might not show anything at all. Some will see a messagebox saying “blah blah blah has been disabled your blah blah blah”
Go back to the GPEDITOR.
You can change the other but make sure you know what you’re doing. And don’t blame me for teaching you about group policy. There are a lot of stuff you can disable and enable using group policy.
(PHOTOS/SCREENSHOTS are available at Pinoy Design E-book vol.1) which can be found at http://pinoydesign.co.cc/ and go to forums you'll find tons of free softwares, tutorials, artworks and media files.
The Power of RUN
Accessibility Controls
access.cpl
Add Hardware Wizard
hdwwiz.cpl
Add/Remove Programs
appwiz.cpl
Administrative Tools
control admintools
Automatic Updates
wuaucpl.cpl
Bluetooth Transfer Wizard
fsquirt
Calculator
calc
Certificate Manager
certmgr.msc
Character Map
charmap
Check Disk Utility
chkdsk
Clipboard Viewer
clipbrd
Command Prompt
cmd
Component Services
dcomcnfg
Computer Management
compmgmt.msc
Date and Time Properties
timedate.cpl
DDE Shares
ddeshare
Device Manager
devmgmt.msc
Direct X Control Panel (If Installed)*
directx.cpl
Direct X Troubleshooter
dxdiag
Disk Cleanup Utility
cleanmgr
Disk Defragment
dfrg.msc
Disk Management
diskmgmt.msc
Disk Partition Manager
diskpart
Display Properties
control desktop
Display Properties
desk.cpl
Display Properties (w/Appearance Tab Preselected)
control color
Dr. Watson System Troubleshooting Utility
drwtsn32
Driver Verifier Utility
verifier
Event Viewer
eventvwr.msc
File Signature Verification Tool
sigverif
Findfast
findfast.cpl
Folders Properties
control folders
Fonts
control fonts
Fonts Folder
fonts
Free Cell Card Game
freecell
Game Controllers
joy.cpl
Group Policy Editor (XP Prof)
gpedit.msc
Hearts Card Game
mshearts
Iexpress Wizard
iexpress
Indexing Service
ciadv.msc
Internet Properties
inetcpl.cpl
IP Configuration (Display Connection Configuration) ipconfig /all
IP Configuration (Display DNS Cache Contents) ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents) ipconfig /flushdns
IP Configuration (Release All Connections) ipconfig /release
IP Configuration (Renew All Connections) ipconfig /renew
IP Configuration (Refreshes DHCP & Re-Registers DNS) ipconfig /registerdns
IP Configuration (Display DHCP Class ID) ipconfig /showclassid
IP Configuration (Modifies DHCP Class ID) ipconfig /setclassid
Java Control Panel (If Installed)
jpicpl32.cpl
Java Control Panel (If Installed)
javaws
Keyboard Properties
control keyboard
Local Security Settings
secpol.msc
Local Users and Groups
lusrmgr.msc
Logs You Out Of Windows
logoff
Mcft Chat
winchat
Minesweeper Game
winmine
Mouse Properties
control mouse
Mouse Properties
main.cpl
Network Connections
control netconnections
Network Connections
ncpa.cpl
Network Setup Wizard
netsetup.cpl
Notepad notepad
Nview Desktop Manager (If Installed)
nvtuicpl.cpl
Object Packager
packager
ODBC Data Source Administrator
odbccp32.cpl
On Screen Keyboard
osk
Opens AC3 Filter (If Installed)
ac3filter.cpl
Password Properties
password.cpl
Performance Monitor
perfmon.msc
Performance Monitor
perfmon
Phone and Modem Options
telephon.cpl
Power Configuration
powercfg.cpl
Printers and Faxes
control printers
Printers Folder
printers
Private Character Editor
eudcedit
Quicktime (If Installed)
QuickTime.cpl
Regional Settings
intl.cpl
Registry Editor
regedit
Registry Editor
regedit32
Remote Desktop mstsc
Removable Storage
ntmsmgr.msc
Removable Storage Operator Requests
ntmsoprq.msc
Resultant Set of Policy (XP Prof)
rsop.msc
Scanners and Cameras
sticpl.cpl
Scheduled Tasks
control schedtasks
Security Center
wscui.cpl
Services
services.msc
Shared Folders
fsmgmt.msc
Shuts Down Windows
shutdown
Sounds and Audio
mmsys.cpl
Spider Solitare Card Game
spider
SQL Client Configuration
cliconfg
System Configuration Editor
sysedit
System Configuration Utility
msconfig
System File Checker Utility (Scan Immediately) sfc /scannow
System File Checker Utility (Scan Once At Next Boot) sfc /scanonce
System File Checker Utility (Scan On Every Boot) sfc /scanboot
System File Checker Utility (Return to Default Setting) sfc /revert
System File Checker Utility (Purge File Cache) sfc /purgecache
System File Checker Utility (Set Cache Size to size x)
sfc /cachesize=x
System Properties
sysdm.cpl
Task Manager
taskmgr
Telnet Client
telnet
User Account Management
nusrmgr.cpl
Utility Manager
utilman
Windows Firewall
firewall.cpl
Windows Magnifier
magnify
Windows Management Infrastructure
wmimgmt.msc
Windows System Security Tool
syskey
Windows Update Launches
wupdmgr
Thursday, April 3, 2008
How to download Video in Youtube and other video hosting site
There's a lot of ways on how to STEAL(joke) or download videos on youtube and other video hosting sites. But this is the easiest way.
1. you have to have Real Player 11.
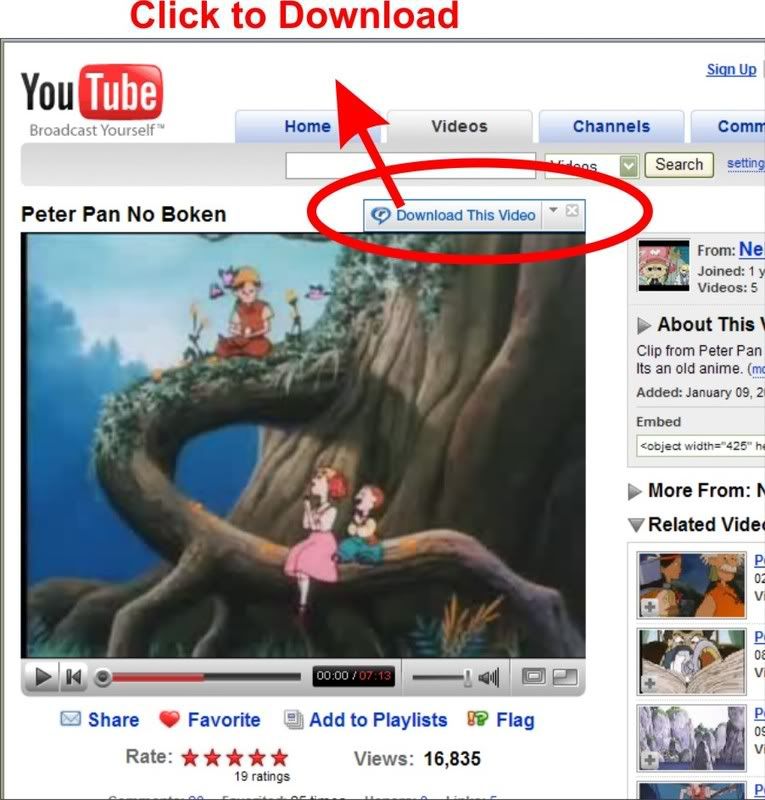
Oh sweet! Look at this: (You're now stealing the video, I mean i'm now stealing it)
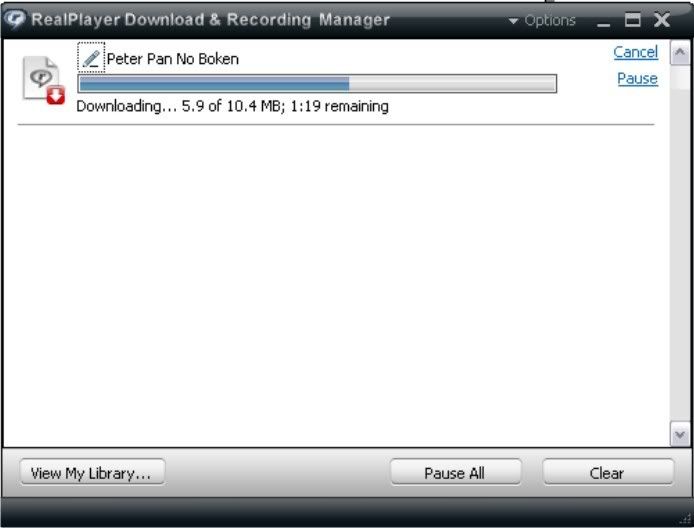
when it's done. open your real player and go to > View > My Library or simply click the View my library button.
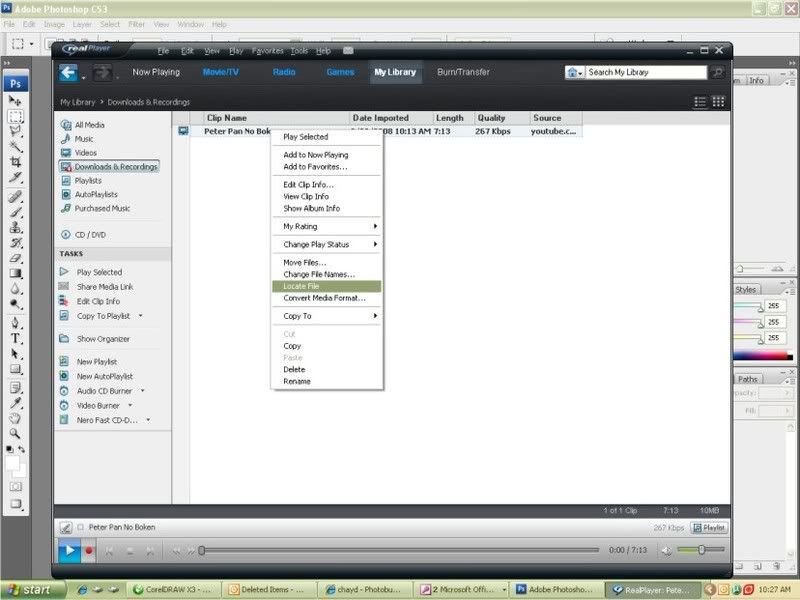 Right click on the video and click Locate file.
Right click on the video and click Locate file.
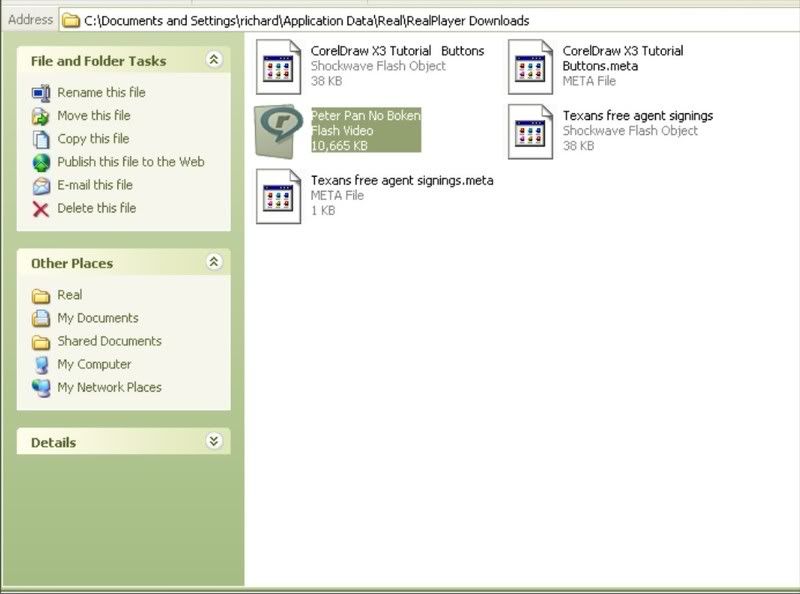 There you have it! Enjoy stealing videos!
There you have it! Enjoy stealing videos!Another Way to download flash video is to download and install Mozilla Firefox: http://www.mozilla.org/download.html. and install this firefox extension called Downloaderhelper: http://www.downloadhelper.net/

